somethings from codeland
Friday, December 30, 2005
Thursday, December 29, 2005
gMail is GREAT
First off if you don't have firefox then you should seriously consider praying and then go to mozilla.com and download it.
If you don't have a gmail account then go get one. Then go get greasemonkey. Now if you don't know, greasemonkey can do just about anything (provided you script the actions out). Its a great way to provide extra functionality to already one of the greatest browsers out there.
Ok so you have a new gmail account, and you have greasemonkey extension installed on firefox. Now you need the scripts installed. Head over to persistent.info and read through what he has to offer. I found the preview bubbles a great help in thumbing through email without having to get out of the inbox view. Another great one to get are the gmail macros. This will provide the functionality of not having to highlight/select all the messages you want to delete and go through the drop down menu to delete messages.
http://persistent.info/ - This guy is really all about greasemonkey scripts.
Wednesday, December 28, 2005
Adobe Reader too Slow
Apache for cygwin
http://httpd.apache.org/docs/1.3/cygwin.html#serv
Use the following statement to install
httpd.exe as a new service:
$ cygrunsrv -I service_name-p /usr/local/apache/bin/httpd.exe
[-a arguments] [-e VAR=VALUE] [-t auto|manual]
[-u user] [-w passwd]
Where -a is used to pass command line
arguments (such as -DFOO defines) to
httpd.exe, and -e is used to pass
environment variables. If necessary you may use the
-t options to set the autostart configuration
for the service. If you want the new service to run under a
different userid, you will have to supply the
-u and -w options.
Starting Apache as a Service
After the new service is installed it can be started
using the following command:
$ cygrunsrv -S service_name
Check your process table and global
error_log file to ensure Apache has started
without any major problems.
Stopping an Apache Service
A running Apache service may be stopped using the
following command:
$ cygrunsrv -E service_name
This will stop all running httpd.exe
processes and shutdown the HTTP service for the
machine.
Removing an Apache Service
An installed Apache service may be removed from Windows
NT or Windows 2000 using the following command:
$ cygrunsrv -R service_name
This will remove your previously defined and installed
service from the machine.
Monitor Bandwidth with iptables
http://www.linux.com/article.pl?sid=05/12/15/177232
Tuesday, December 27, 2005
Thursday, December 22, 2005
Wednesday, December 21, 2005
Monday, December 19, 2005
torrentflux
torrentflux
Reflection like Apple...
Check the source on the demo link...
What it does...

image reflect on background canvas...
Nero Scout - be gone...
this little program grabs all your music files and puts them all in a database....
article for more...
go to start and click run. Then type copy and paste the following and hit run:
regsvr32 /u "%COMMONPROGRAMFILES%\Ahead\Lib\MediaLibraryNSE.dll"
Sunday, December 18, 2005
Saturday, December 17, 2005
Another geek site
TWAT radio
Friday, December 16, 2005
Ruby on Rails

Ruby = another web development language
rails = framework to integrate with a database architecture
radrails = ruby ide
four days on rails - a ruby on rails production howto
I like how the emphasis is not on the setup. Its not long and drawn out. Its easy to dive into the language. Interesting way to develop...
Wednesday, December 14, 2005
Control iTunes from a web Browswer
Install a web server and Control iTunes via webpage...
Turn your laptop into the ultimate controller...
Guide
Tuesday, December 13, 2005
iPod mini mod: Storage and Battery Upgrades
Sunday, December 11, 2005
Design: Rounded edges
I like the layout...
Friday, December 09, 2005
msconfig used to be...
from digg
"This utility has the most comprehensive knowledge of auto-starting locations of any startup monitor. You'll probably be surprised at how many executables are launched automatically. It shows you what programs are configured to run during system bootup or login, and shows you the entries in the order Windows processes them, and it's by Sysinternals!"
http://www.sysinternals.com/utilities/autoruns.html
Windows Passwords revealed faster
http://blog.tech-security.com/?p=15
WPA wireless cracking tools
http://wifinetnews.com/archives/004428.html
Sunday, December 04, 2005
tweaking windows
http://www.connectedinternet.co.uk/blog/_archives/2005/12/5/1434755.html
Thursday, December 01, 2005
Wednesday, November 30, 2005
Monday, November 28, 2005
Saturday, November 26, 2005
The picture guy within
Picasa - from Google
Thursday, November 24, 2005
open source magazine = free
usb/ip project
Monday, November 21, 2005
bandwidth aggregation
anyone have a neighbor with wifi???
Friday, November 18, 2005
mysql on cygwin
and here are the instructions: http://dev.mysql.com/doc/refman/5.0/en/installing-source-tree.html
Color MatchMaker...
Friday, November 11, 2005
Tuesday, November 08, 2005
ssh on windows
A good tutorial
Monday, November 07, 2005
Get money for that Tech Support
A good idea on how you can use Ultra VNC and your own website to start making money for all that tech support that you do...
Monday, October 24, 2005
Sign up for free Spam
Ok so someone is just really irritating...
Kill their inbox with almost every spam database ever... (most of them don't even verify, they just start sending out...)
Monday, October 17, 2005
AJAX revolution...
I would say with maturation this language posseses what the web needs to keep on top of the game of web fashion, while still providing adequate measures of reliablity to still offer the substance sites provide to date. This provides a lot more bells and whistles, giving web developers the options needed to develop a true unique solution or sense of style.
"Browsers whose JavaScript Interpreters provide the XMLHttpRequest object can make nonblocking calls back to the server. The server can return peices of HTML to be displayed, JavaScript to be run by the browser, or indeed any data you like."
-Rick Wayne of Software Development magazine
Mr. Waynes latest craze is integrating AJAX into his future productions utilizing a dynamic scripting solution called Ruby on Rails. This open source platform integrates easily with database architecture (mostly automating the process for you) and is not hard to pick up. Making that latest idea come to life with the latest technology web programming and design has to offer is only getting better. At least check it out, so you're not left behind.
For more on Ruby on Rails with AJAX check out O'Reilly
from the AJAX wiki
Articles
- Compilation of AJAX articles, by Robson Junior
- Ajax: A New Approach to Web Applications, by Jesse James Garrett. The original article which coined the term
- Beginners Guide to Ajax A quick no-nonsense tour of the fundamental Ajax principles, with example code
- Ajax: Usable Interactivity with Remote Scripting Introduction on how to use Ajax
- Guide to Using XMLHttpRequest (with Baby Steps) Tutorial by Bill Bercik introducing XmlHttpRequest
- Implementing Ajax in ASP.NET using the Ajax.NET wrapper by Karl Seguin
- Rasmus' 30-Second AJAX Tutorial A simple but functional example and ad hoc tutorial posted by Rasmus Lerdorf of PHP fame.
- AJAX:Getting Started Article by Mozilla.org.
- State of Ajax: Progress, Challenges, and Implications for SOAs
- Ajax's Achilles Heel maps.google.com with Javascript disabled
- Why Ajax Matters Now by Jesse James Garrett
- Ajax gives software a fresh look Blurring the line between desktop and Web applications.
- Ajax for Java developers: Build dynamic Java applications IBM developerWorks Article by Philip McCarthy
- Javascript Refactoring for safer, faster, better AJAX by Pavel Simakov
Wednesday, October 12, 2005
Web 2.0 Explained
Tech aspects:
O'Reilly
Web 2.0 Conference
Technology Review an online MIT publication
http://www.oreillynet.com/pub/a/network/2005/10/06/barry-diller-opens-web-20.html
http://paulmiller.typepad.com/thinking_about_the_future/2005/08/thinking_about_.html
http://internetalchemy.org/
examples of the future: bindows.net
What this means to you:
| No expensive operating systems | No going back and forth with files to print out or something like that (as long as a computer has an internet connection, you have access to your entire office space... | This could mean major savings for the corporate computing structure (if a secure solution was implemented in-house) I think this is going places. You dont have to have people off with Laptops equipped with expensive software, all you need is a tunnel to the internet. Just a browser that runs on a locked down operating system. So much for document viruses... We just have to have reliable servers, that experience little to no downtime and this "coming of the future" will be the future... |
Sunday, October 09, 2005
os x86 anyone???
Are you ready to join the cult and harness the simplicity of stable computing? I think I'll dive in permanently when the intel chips start making their debut...

http://www.osx86.theplaceforitall.com/howto/
Friday, October 07, 2005
a Linux Firewall Solution
Saturday, October 01, 2005
a quick word on headphones
stay away from these:

These rock so go for it...

Wednesday, September 21, 2005
Opera for free
Check it out:

Update: Pages that don't render properly in Firefox are mainly becuase the code for the site does not adhere to the standards of the www
Big companys (ie Microsoft, Yahoo, etc.) hate standardization. Mainly becuase it means that they have to compete on the same ground as the next guy. If you have a huge customer basis already, then why standardize and give people an easy alternative to convert to???
Tuesday, September 13, 2005
Ebay Buying Skype?
Wednesday, September 07, 2005
Saturday, September 03, 2005
Super Notebook kicks serious ass...

SPECIFICATION:
Processor: 6.8GHZ CPU (AtomChip® Quantum® II processor or 4 x Intel® Pentium® M processors 1.7CHz) / System Compliance: Two Operating Systems with Voice Command (Microsoft® Windows® XP Professional and Linux®) / Memory: 1TB Quantum-Optical non-volatile RAM (NvIOpSRAM-SODIMM 200-pin) / Storage: 2TB non-volatile Quantum RAM (NvIOpRAM-ATA IDE) / Optical Drive: DVD Super Multi / LCD Display: 12.1” WXGA (1280 x 800, 16:10) TFT Glare Type LCD display with 1.3 Mega pixel CMOS camera / Video & Graphics: Two Integrated graphic controllers [Intel®855GME internal graphics, support Intel® DVMT (Dynamic Video Memory Technology) and AtomChip® DVM (Dynamic Video Memory)] / Communication: 10/100 Base-T LAN on board, MDC Fax/Modem V.90/V.92 on Board, 802.11a/802.11b/802.11g WLAN, Intel® PRO/Wireless 2100/2200BG/2915ABG network connection, WiFi, Bluetoth, GPRS -with Bluetoth antena, CMOS camera with USB interface, Mega pixel resolution CMOS image / Pointing Device: Synaptics touchpad with 4 way scrolling button / Application Launch Key: E-mail, Internet, Capture, WLAN / LED Status Indicator: Power, Suspend/Resume, Battery Charging Status, Quantum Storage Access, Num Lock mode, Caps Lock mode, Scroll Lock mode, WLAN Lock mode / Keyboard: 3.0mm travel, inverted-T, 88keys with 2 windows key (Internet & Microsoft For Connectivity) / Interface Ports Front Side: One 4-in-1 card reader slot (support SDIO/SD/MS Pro/MS), Audio line out, Stereo Microphone-in / Interface Ports Left Side: LAN port, Modem port, SVGA–out port, One Type II PCMCIA slot (support CardBus), 1394A port (mini jack) / Interface Ports Right Side: USB 2.0 ports x 3 / Interface Port Rear Side: DC-in, Kensington Lock / Audio: Built-in two stereo speakers and Built-in Microphone / AC Adapter (Input: 100-240V AC, 50-60Hz, 1.5A. Output: 20V DC, 2.5A, 50W) / Battery: 6 cell Li-lon battery pack. Battery Charge: 3 hrs charge time to 100% capacity while system off and 4 hrs charge time while system on. Battery Life: Approximately 8 hours for AtomChip® Quantum® II processor and 3 hours for 4 x Intel® Pentium® M processors 1.7CHz / BIOS: AMI, Support PnP, password, Bootable from USB and DVD / Power Management: ACPI 2.0 compliance / Smart Battery System Support / Security: Kensington Lock / Size: 320.0(W) x 242.0(D) x 22.0(H)mm/28.0mm (front/back) / Weight: 1.9kg(when fully equipped with AtomChip® Quantum® II processor) and 2,20kg(when fully equipped with 4 x Intel® Pentium® M processors) / Packing Accessories: Quick Guide, Support CD (Driver, Utility, Manual), AC Adapter, Power Cord, Battery Pack, BOSE Headphone Music System with noise Cancelling.
Wednesday, August 31, 2005
USB Car key!?

I think that its an awesome idea: Mazda's new hatchback is to open your door, start your car, add music to the car's internal hard drive, and provide a means for loading GPS Maps. I think that this will be my next vehicle definetly. Like the guy that wrote this article,"Good thing this is still a production car, and my [truck] is still running good.
http://www.japancorp.net/Article.Asp?Art_ID=10779
Monday, August 29, 2005
Knoppix Arcade Machine
Knoppix Mame will turn any machine into a sweet arcade machine. Sounds great for my little brothers and sisters...
The original package can be found on sourceforge, but I would say its a hell of a lot easier just downloading off of exeem or demonoid. (torrents) If you go with the original package then you still have to add your own roms to the distro and rebuild, whereas if you go do a search for "mame" on a torrent network of some kind, its already there. But hey if you dont have anything better to do then have fun.
Friday, August 26, 2005
Identity Thieves in Action: Video

http://www.identitytheftsecrets.com/videos/paypalemail3.html\
Interesting to see how these guys go through this process...
Detect weak network passwords with Hydra
passwords for network applications, and change them often, but you know
that not everyone on your network is security-conscious. Starting to
worry that weak passwords may be slipping through your defenses? Then
it's time to unleash Hydra, a network login cracker for more than 30 network services.
Hydra comes from The Hacker's Choice
(THC), a group that has written more than 60 open source network
security tools and research papers. Hydra receives frequent updates and
is the group's second most downloaded project.
I ran Hydra against a MySQL server on my local machine. The simplest
way to run Hydra is to specify a user name and password combination for
it to try. This is useful only when you know what the username or
password of the service is likely to be. To get a feel for Hydra, use a
login and password that you know will succeed. I did so by running:
hydra localhost mysql -l root -p rootpass
This runs Hydra against MySQL on the local machine with a login of root
and a password of rootpass. By default, Hydra spawns 16 concurrent
processes. Adding more processes with the -t
option can speed things up a bit at the risk locking yourself out of a
network service if the administrator restricts the number of connection
attempts. Here, Hydra reports it succeeded in connecting with this
combination and outputs:
[3306][mysql] host: 127.0.0.1 login: root password: rootpass
To run Hydra against a machine on a network, just substitute localhost with an IP address or hostname.
Specifying a login and password combination for every attempt is not
very efficient. The login part of the equation is the easy one. Typical
logins for most network services are words like root or admin. The
password part is where the difficulty lies. That is what makes Hydra's
ability to use dictionary files for both logins and passwords so
useful. A dictionary file contains a list of words (one word per line)
that Hydra can cycle through for logins or passwords.
You can specify a dictionary file with the following syntax:
hydra localhost mysql -L login.txt -P pass.txt
Hydra does not come with any dictionary files -- you must
create your own or download one. One option is to use something like an
English language thesaurus
from Project Gutenberg. This list contains commas and does not have
only one word per line. You can clean up this list with the following
Sed command:
sed -e 's/,/ /g' -e 's/[ ]/\n/g' mthesaur.txt | sort | uniq > pass.txt
This removes the commas, places each word on its own line, and removes
duplicate entries. This gives you a dictionary file with 74,618 words.
One way to test Hydra with a file this size is to create a small
login dictionary file with usernames and use a large dictionary file
for passwords. Next, add a MySQL account with a username and password
combination from these files. For example, using a login dictionary
file with 10 entries and pass.txt gives Hydra 746,180 combinations to
cycle through.
If you know the service you're testing against has a minimum
password length -- say, passwords must be at least 10 characters long
-- then testing passwords with fewer than 10 characters would be a
waste of time and resources. Hydra comes with pw-inspector, a utility
that sorts passwords based on criteria you pass to it. You can sort
pass.txt to words with 10 or more characters, by running:
cat pass.txt | pw-inspector -m 10 > sortedpass.txt
This trims the list down to 28,571 words. The final command to run is:
hydra localhost mysql -L logins.txt -P sortedpass.txt
This brings down the number of combinations to a slimmer 285,710.
The amount of time this takes depends on the speed of your machine
and the placement of the login and password in the files. Hydra updates
you as the process goes on. My 1.2GHz AMD Duron processor can crunch
approximately 4,000 combinations per minute with an estimated time of
one hour 10 minutes to run the whole set. This particular scan took an
hour. I achieved nearly the same result over a switched 100Mbps network
in later testing. In that test, Hydra's bandwidth usage averaged
100Kbps. If you need to quit mid-scan, go ahead. Hydra saves its
results in a file named hydra.restore. To pick up where you left off,
use the command hydra -r from within the directory where you initiated the scan.
There is much more to Hydra then what these simple examples show.
Hydra can scan entire networks at a time and work through proxy
servers. A GTK-based graphical interface called xhydra is also
included.
With the help of Hydra, you can weed out the weak logins and
passwords that pose a security threat to your network. It's a good tool
in your network security arsenal.
Paul Virijevich is working to eliminate the "Linux consultants cost more" TCO myth. He recently started a consultancy, providing cost-effective open source solutions to small businesses.
Saturday, August 20, 2005
DVD Shrink
Nessus Vulnerablity Assesment
For the windows boys...
Windows Nessus
Just straight off the Auditor boot cd
http://new.remote-exploit.org/index.php/Auditor_main
How to use it:
Iron Geek on Nessus
He's got a speech issue but the guy is damn brilliant
If you're thinking I should have to put the link for a nessus download in linux then maybe you shouldn't be using linux...
The ultimate hack
- Go and grab a GSM transciever and rig it up with an asterisk linux based pbx box.
- Make the pbx talk VOIP (Work your system out with a VOIP carrier...)
- Have your GSM phone talk to the transciever and send your calls through the PBX via IP
- Start saving a crapload on calls..
found somewhere on slashdot
Wednesday, August 17, 2005
HTTP headers explained
fun with http headers
Friday, August 12, 2005
password recovery
http://www.passwordportal.net/
Have you lost or forgotten a password? Do you need help recovering a password? Here you will find links to Commercial Password Recovery resources.
Newsgroups: Faster downloads
Newsgroup download tutorials. They have a movie with some helpful search sites for material. Definitely worth looking into if you are even somewhat interested in awesome download speeds...
Myth (TV)ology
This prog plays well on Fedora Core 3
http://wilsonet.com/mythtv/fcmyth.php
Although I have found a mythKnopp version. (installs a myth tv system straight off of one distro installation disc...
KnoppMyth Torrent

Systm did an episode on a MythBox. All you need is a 2.0ghz machine with 512 mb ram, as much storage as you think you need (80gb is sufficient), and one or two tv tuner cards and you're in shape for some HDTV picture in Picture tivo session whatever.
Thursday, August 11, 2005
podcasts galore
...and there is a podcast no matter what your flavor of preference is over at Odeo.com
Tuesday, August 09, 2005
WRT54G Firmware and WDS

WDS- Wireless Distribution System
By default, the stock firmware on the WRT54G does not support a whole list of features that it is capable of...
... and despite Sveasoft charging for their supped up version of the firmware its out under GPL protection circulating. Apparently they have been kicking people off of their subscriptions if they find that you link out to one of the GPL download sites.
WRT54G Forum
WDS Tutorial
WRT54G firmware Download Site Download
Sveasoft
Subnetting WDS
Open WRT Download
Open WRT Documentation
SQUID Proxy Server
Goals:
- Transparent Proxy (no configuration required on browser)
- A password for access (one generic password)
- Keyword filter lists (block out all the crap out there)
The network topology should prove interesting as well. I am going to spread wireless throughout the house. I will have to play with the setup, but it should work something like this: I will have the line running into the house, which will then run into a WRT54G. That one unit will run all http traffic (port 80) to the squid proxy server box. Then the box will be setup to intercept all http traffic, filter it, and cache results and forward pages to client browser. Not sure how to make http traffic go through squid without setting the box as a gateway.
Links
Transparent Proxy
Squid config info
Squid Home,
www.squid-cache.org
Squid
Documentation Project, squid-docs.sourceforge.net
Squid Browser Conf Info
For Proxy
Authentication,
home.iae.nl/users/devet/squid/proxy_auth
Sunday, August 07, 2005
SNMP Protocol Analyzers
Friday, August 05, 2005
Free Tech Support
http://www.protonic.com/
Thursday, August 04, 2005
Forensics with Linux: White Papers
http://www.crazytrain.com/papers.html
http://www.crazytrain.com/dd.html

knoppix std 0.1 has everything you will need to hack or commit otherwise blackhat acts...
knoppix STD 0.1 => torrent
Wednesday, August 03, 2005
Monitor Servers
ZABBIX
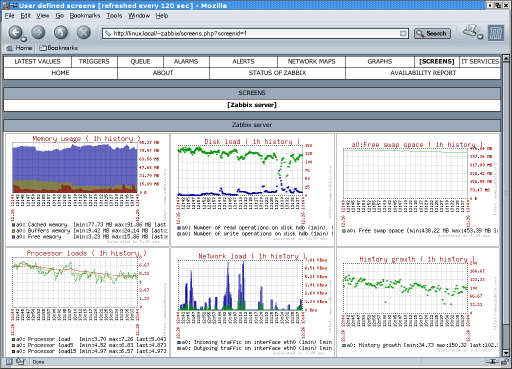
(they both have excellent reporting capability)
They both utilize web serving capabilities to shoot out dynamic pages. I do believe that all programs will at least have some form of an interface in this fashion. The internet is due for an addition of another dimension... Flash is a good intro to what I am talking about... (something a little more capable of taking some popularity off of the television)
Nagios
Zabbix
Tuesday, August 02, 2005
Web Templates
So I've heard of:
pMachine
sixapart.com (based more so for web bloggers)
Moveable Type
TypePad
LiveJournal
(I'm sure there are thousands more)
So yes, Web Design proves to show interest in my future...
Commenting your code...
http://particletree.com/features/successful-strategies-for-commenting-your-code
Tips from MSDN on Commenting Code
How to size text using ems
http://www.clagnut.com/blog/348/
Monday, August 01, 2005
Web Design: Absolute Positioning
http://www.academystudios.com
http://www.dotfive.com
Sunday, July 31, 2005
Port reference info
http://www.iss.net/security_center/advice/Exploits/Ports/default.htm
Port 113: ident seems of interest (although blocked by default on most firewalls)
Intriguing Web Design

I have long since kept up with Kevin Rose and the appeal he brings to new technology. I recently learned of a social bookmarking system that he implemented called digg. Just digging around in there, I learned of a design group by the name of StopDesign, which has a refreshingly clean balance between design and pure data.
http://stopdesign.com/
http://www.mikeindustries.com/blog/archive/2005/07/make-your-site-mobile-friendly
http://microformats.org/
http://live8.technorati.com/
http://www.flickr.com/photos/simplebitsdan/sets/663014/
Graphics and Linux
This has to be one of the coolest looking sites that I have found in quite some time. They promote 3D graphics and animation.
Something definately worth considering looking into. Slashdot has an article titled Disney, DreamWorks, Pixar Go Linux. Supposedly Linux is the best platform for higher end graphic design, most likely because of the lack of memory issues that windows seems to be plagued with.
Linux is looking sweeter and sweeter. If you are not a gamer then I suggest looking into Fedora Core 4 with KDE 3.5. Not only is it a cleaner/smoother interface but it will probably make you more productive in the end.
KDE is very similiar to the windows graphical user interface (GUI). However I prefer Gnome, because of its simplicity. It supports everything that I work with: mainly Firefox, abc torrent client, ssh command shell (for server configurations). Other than that I do have a little Dell Inspiron 700m that does run windows xp. Reason being that most of the clients I work with are on windows environments (making it easier to operate in a Microsoft Shop). I do have VMWare running a fedora core installation, which I do use to test the sites and database applications that I design. I would like to look further into some other distrobutions of linux however: namely Gentoo, Debian, and Solaris.
America handing the Tech torch away???
Does Globalization of the Scientific/Engineering Workforce Threaten U.S. Economic Leadership? This paper develops four propositions that show that changes in the global job market for science and engineering (S&E) workers are eroding US dominance in S&E, which diminishes comparative advantage in high tech production and creates problems for American industry and workers: (1) The U.S. share of the world's science and engineering graduates is declining rapidly as European and Asian universities, particularly from China, have increased S&E degrees while US degree production has stagnated. 2) The job market has worsened for young workers in S&E fields relative to many other high-level occupations, which discourages US students from going on in S&E, but which still has sufficient rewards to attract large immigrant flows, particularly from developing countries. 3) Populous low income countries such as China and India can compete with the US in high tech by having many S&E specialists although those workers are a small proportion of their work forces. This threatens to undo the "North-South" pattern of trade in which advanced countries dominate high tech while developing countries specialize in less skilled manufacturing. 4) Diminished comparative advantage in high-tech will create a long period of adjustment for US workers, of which the off-shoring of IT jobs to India, growth of high-tech production in China, and multinational R&D facilities in developing countries, are harbingers. To ease the adjustment to a less dominant position in science and engineering, the US will have to develop new labor market and R&D policies that build on existing strengths and develop new ways of benefitting from scientific and technological advances in other countries. http://www.nber.org/papers/W11457 |
Apparently South Korea is the best of the best right now, in terms of higher education. I am actively searching for the other side of this story...
It has been said that some of the programming jobs that went to India are coming back because of both the difficulties with international relations, and introductory assesment of interfacing with existing code and system operations. This is soothing, that while there is a knowledge of a presense of white collar outside of the U.S. its still not dominant as of yet. There is still a chance of changing the way Americans view the current situation, work to achieve a solution, and learn so as to accomidate what we have been lacking for so long.
CAN AMERICANS COMPETE? Is America the World's 97-lb. Weakling? In the relentless, global, tech-driven, cost-cutting struggle for business, America isn’t ready—here’s what to do about it. By Geoffrey Colvin uncle sam (Illustration: R. Sikoryak) It’s a crisis of confidence unlike anything America has felt in a generation. Residents of tiny Newton, Iowa, wake up to the distressing news that a Chinese firm—What’s it called? Haier? That’s Chinese?—wants to buy their biggest employer, the famed but foundering Maytag appliance company. Two days later, out of nowhere, a massive, government-owned Chinese oil company muscles into the bidding for America’s Unocal. The very next day a ship in Xinsha, China, loads the first Chinese-made cars bound for the West, where they’ll compete with the products of Detroit’s struggling old giants. All in one week. And only two months earlier a Chinese company most Americans had never heard of took over the personal computer business formerly owned—and mismanaged into billions of dollars of losses—by the great IBM. "Can America compete?" is the nation’s new No. 1 anxiety, the topic of emotional debate in bars and boardrooms, the title of seminars and speeches offered by the liberal Progressive Policy Institute, the conservative economist Todd Buchholz, and countless schools and Rotary Clubs. The question is almost right, but not quite. We’re wringing our hands over the wrong thing. The problem isn’t Chinese companies threatening U.S. firms. It’s U.S. workers unable to compete with those in China—or India, or South Korea. The real question is, "Can Americans compete?" continued http://www.fortune.com/fortune/articles/0,15114,1081269,00.html |
Engineering @ OSU
I am now officially an undergraduate Engineering Major at OSU. I have a really decent schedule with the exception of one CAD engineering teacher. He, supposedly, doesn't communicate very well, and assign's vague tasks that he expects certain aspects centralized upon. Well, bring on the new technology...
nmap

http://www.insecure.org/nmap/lamont-nmap-guide.txt
http://members.dodo.net.au/~ps2man/Nmap/nmap.html
http://moonpie.org/writings/discovery.pdf
Customize the Right click menu
http://www.jfitz.com...s/rclick_custom.html
Encryption on VNC Connection
http://home.comcast.net/%7Emsrc4plugin/
KnoppMyth

Systm did an episode on a MythBox (tivo without the subscription fees) All you need is a 2.0ghz machine with 512 mb ram, as much storage as you think you need, and one or two tv tuner cards and you're in shape for some HDTV picture in Picture tivo session whatever. So its good times yet again. Fight the bastards that sold you the service to get rid of commercials only to have you watch some as you fastforward through the bs. If you have the box, the software side of it is really easy (pretty much plug-n-play) Make sure you have a blank disk, and then you can go off about the whole enter, next, enter, next etc....
KnoppMyth Torrent
ZipIt!
So this is the gadget of the hour...
Apparently you can through a better linux distro and load an ssh client... Have the capacity to control servers on a little handheld chatting device...
LinuxDevices has some good info on everything...
keyboard screen?
Saturday, July 30, 2005
FireFox insight
Friday, July 29, 2005
Google Earth
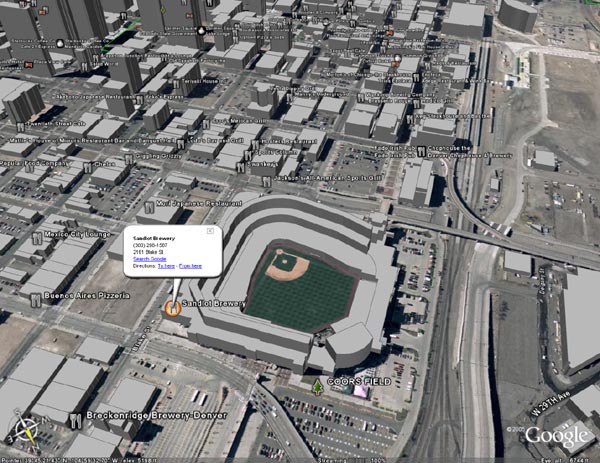
I hope that Google Earth doesn't start linking up with cell phone
companies to start reporting live gps signals of cell phones... Or
there will be a lot of little pissed off teenagers and left wing nut
cases. GPS is still to be argued though. There is no doubt that the
NSA, not the CIA, (NSA is charged with security and communications)
tracks everything that they possibly can, including things we probably
have no clue have any realm of traceability. Just in talking with a
friend programmer at Boeing. I know that technology offers so much more
of a broad spectrum of features.
Oh yeah, the program is free...
Google Earth Plus
Twitter Updates
About Me

- Rueben
- I have been working with computers/programming to put myself through college since I graduated high school. I am currently attending Oklahoma State University for bachelors degree in biological sciences. Along with my experience in programming, a degree in biology will allow me to pursue a career in bioinformatics research concerning genetic diseases (i.e. cancer).
Blog Archive
-
►
2009
(14)
- ► 02/08 - 02/15 (1)
- ► 02/01 - 02/08 (1)
- ► 01/25 - 02/01 (1)
- ► 01/18 - 01/25 (9)
- ► 01/11 - 01/18 (2)
-
►
2008
(35)
- ► 12/28 - 01/04 (8)
- ► 12/21 - 12/28 (4)
- ► 11/30 - 12/07 (1)
- ► 11/16 - 11/23 (1)
- ► 11/09 - 11/16 (2)
- ► 11/02 - 11/09 (2)
- ► 10/26 - 11/02 (2)
- ► 10/19 - 10/26 (7)
- ► 10/12 - 10/19 (3)
- ► 10/05 - 10/12 (4)
- ► 09/28 - 10/05 (1)
-
►
2007
(119)
- ► 11/04 - 11/11 (3)
- ► 10/28 - 11/04 (7)
- ► 10/21 - 10/28 (2)
- ► 10/14 - 10/21 (3)
- ► 10/07 - 10/14 (1)
- ► 09/30 - 10/07 (6)
- ► 09/23 - 09/30 (6)
- ► 09/16 - 09/23 (8)
- ► 09/09 - 09/16 (2)
- ► 09/02 - 09/09 (3)
- ► 08/26 - 09/02 (3)
- ► 08/19 - 08/26 (3)
- ► 08/12 - 08/19 (8)
- ► 08/05 - 08/12 (6)
- ► 07/29 - 08/05 (2)
- ► 07/22 - 07/29 (2)
- ► 07/15 - 07/22 (1)
- ► 07/08 - 07/15 (1)
- ► 07/01 - 07/08 (2)
- ► 06/24 - 07/01 (8)
- ► 06/17 - 06/24 (1)
- ► 06/10 - 06/17 (9)
- ► 06/03 - 06/10 (6)
- ► 05/27 - 06/03 (3)
- ► 05/20 - 05/27 (1)
- ► 05/13 - 05/20 (2)
- ► 05/06 - 05/13 (7)
- ► 04/22 - 04/29 (3)
- ► 04/15 - 04/22 (4)
- ► 04/08 - 04/15 (1)
- ► 04/01 - 04/08 (2)
- ► 03/25 - 04/01 (2)
- ► 03/18 - 03/25 (1)
-
►
2006
(51)
- ► 12/31 - 01/07 (1)
- ► 12/10 - 12/17 (1)
- ► 12/03 - 12/10 (1)
- ► 11/19 - 11/26 (1)
- ► 11/05 - 11/12 (3)
- ► 10/29 - 11/05 (1)
- ► 10/22 - 10/29 (3)
- ► 02/26 - 03/05 (4)
- ► 02/19 - 02/26 (8)
- ► 02/12 - 02/19 (7)
- ► 02/05 - 02/12 (6)
- ► 01/29 - 02/05 (1)
- ► 01/22 - 01/29 (7)
- ► 01/15 - 01/22 (3)
- ► 01/08 - 01/15 (3)
- ► 01/01 - 01/08 (1)
-
▼
2005
(100)
- ▼ 12/25 - 01/01 (8)
- ► 12/18 - 12/25 (11)
- ► 12/11 - 12/18 (7)
- ► 12/04 - 12/11 (5)
- ► 11/27 - 12/04 (5)
- ► 11/20 - 11/27 (6)
- ► 09/04 - 09/11 (1)
- ► 08/28 - 09/04 (4)
- ► 08/21 - 08/28 (3)
- ► 08/14 - 08/21 (5)
- ► 08/07 - 08/14 (10)
-
►
07/31 - 08/07
(20)
- Free Tech Support
- Forensics with Linux: White Papers
- Monitor Servers
- Web Templates
- Web design tutorials blog
- Security Webinars
- Commenting your code...
- How to size text using ems
- Web Design: Absolute Positioning
- Port reference info
- Intriguing Web Design
- Graphics and Linux
- America handing the Tech torch away???
- Engineering @ OSU
- nmap
- Customize the Right click menu
- Encryption on VNC Connection
- KnoppMyth
- ZipIt!
- keyboard screen?




